
How Stephen Gould Scaled Its Capacity by 30% without Making a Single Hire
Collaboration tools security is of paramount importance in today's digital world. It's where we work on projects, share documents, and communicate in real time, regardless of physical location. Their usage has increased dramatically over the past few years, with over 16% of the total employees working remotely and 62% working hybrid.
In this paper, we discuss the steps to avoid cyber threats and attacks, sensitive data breaches, financial loss, and reputational damage for organizations. We also examine how you can protect your company while collaborating in an all-in-one digital workplace, sharing sensitive information, and keeping all conversations and data together.

Fill out the form to continue reading
While collaboration tools have revolutionized how we work, their increased use also brings various security risks that businesses must address to safeguard their data and systems.
Here are some of the most significant security risks associated with collaboration tools.
Several real-world examples highlight the risks of using collaboration tools. In 2018, Marriott International suffered a data breach that affected up to 500 million guests, including names, contact information, and passport numbers. The breach resulted from unauthorized access to the company’s guest reservation database using compromised employee login credentials.
A similar thing occurred in the 2020 security breach of the platform Zoom. The breach resulted in the theft of login credentials for over 500,000 accounts, which were then sold on the dark web.
Collaboration tools that put security first typically offer various security measures to mitigate these risks, such as end-to-end encryption, two-factor authentication, and access controls. However, the effectiveness of these measures depends on their implementation and user awareness.
You most likely depend on your collaboration tool daily if you’re part of the remote or hybrid workforce. Security is still needed even if you’re working in the same physical office as your colleagues. Collaboration tools are one of the favorite targets of cybercriminals who seek to gain access to sensitive data, such as confidential company information or customer data.
So why are collaboration tools so often targeted for data breaches?
Everyone shares sensitive information in their collaboration tool, such as confidential business plans, customer data, passwords, and financial information. If there isn’t proper security, hackers can gain unauthorized access to this data, leading to data breaches and other security incidents.
Information is money. Customers, partners, and other stakeholders expect organizations to secure the information they share since it’s almost always highly confidential. Top-notch security features such as encryption and access controls can help prevent unauthorized access.
Collaboration tools are often used to share files and communicate with people outside of an organization’s network. This has made them a more attractive target for cybercriminals who search for vulnerabilities and use them for financial gain.
Overall, if you prioritize collaboration tools security, you can enjoy the benefits of increased productivity and collaboration while minimizing the risk of security incidents.
So how can you keep all your data, conversations, essential files, and confidential projects safe? Some sources can tell you exactly how to ensure safety – for example, the National Institute of Standards and Technology (NIST) has published guidelines for securing collaboration tools in a remote work environment. The guidelines emphasize the need for strong authentication and access controls, encryption, and regular security assessments.
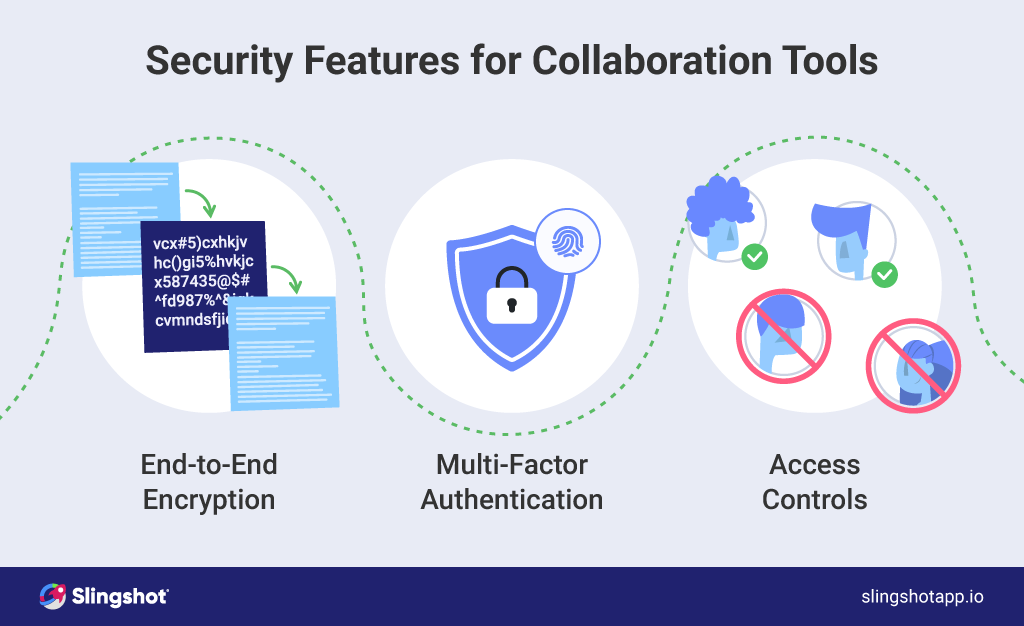
End-to-end encryption ensures that data is protected in transit and at rest, preventing unauthorized access. Encrypted data turns text into unreadable characters so that only authorized readers can consume it. Even if hackers intercept the data, they cannot read or understand it.
Multi-factor authentication requires multiple forms of identification to prevent unauthorized access, even if a password is compromised. Additional identification methods include a password, fingerprint, password, and security token.
Access controls allow administrators to limit the access of specific users or groups to certain data or functionalities. User permissions help prevent unauthorized access to sensitive information or essential functionalities that could disrupt workflow.
To mitigate these risks, the collaboration tool you choose should implement these features to ensure the safety of sensitive data and prevent unauthorized access.
Slingshot can ensure security for its users by implementing the following measures:
Slingshot empowers your team to produce extraordinary results that drive business growth – with a high priority on security. In Slingshot, internal and external team members collaborate with different access levels to protect sensitive information about projects.
Here is a bit more about Slingshot’s security:
Slingshot implements end-to-end encryption to ensure that all data transmitted and stored on the platform is encrypted and only accessible by authorized parties. Through Amazon Web Services (AWS), Slingshot enables secure collaboration for your team without needing a corporate VPN.
We require users to provide additional verification steps beyond just a password to access their account. This adds an extra layer of security against unauthorized access.
Slingshot supports a single-tenant database that allows organizations to choose the country or region where to store their encrypted data at rest. Currently available (US, Europe, Japan) within the Enterprise version of Slingshot. Cloud data is stored in the State of Virginia (US) and the Republic of Ireland (EU) since November 2022.
Your collaboration tool should be your haven regarding data, files, conversations, and sensitive project information. That is what we build this all-in-one digital workplace on – prioritizing security and finding the best way to boost your results in the meantime.
See how Slingshot can help you and your teams do more of their best work.